Is iOS 16 the new digital fortress?
iOS 16 implements new security features: Passkeys and Lockdown mode. Read why they matter, and of course the weekly dose of tech, cybsersec news and resources

This week iOS 16 has been released to the public. I am not going to enumerate every new feature, you can already find lots of other sources that have done that. I just want to focus and got into detail on two new security features: Passkeys and Lockdown mode.
Passkeys
Apple Passkeys are Apple’s implementation of WebAuthn standard. WebAuthn is a web credential standard API initially proposed by the FIDO alliance and later standardized by the W3C.
This protocol is aimed at substituting password based authentication, and instead it proposes cryptographic based authentication mechanisms, a much more secure way of authenticating on the Internet. It uses Public key cryptographic mechanisms, where for each credential a couple of keys are created. The public key is shared with the web service and the private key is kept secret in the authenticator device.
At the moment of performing the authentication against the web service, a challenge is sent through the browser, which acts as a mediator between the web service and the authenticator device.
The authenticator is the device that holds the private key and is the one that resolves the authentication challenge at the moment of login. In the case of Apple, the keys are protected by either TouchID or FaceID, that is, by a biometric authentication. This means that only the intended user will be able to authenticate with the keys that are stored in the device. No secrets are shared between the web service and the authenticator. This makes this technology highly phishing resistant.
Apple offers the possibility of saving the private keys to iCloud Keychain, which is end-to-end encrypted, enabling the possibility of having the keys synchronized in all your Apple’s devices.
Apple is able to make its users adopt this new technology very fast in a very convenient way. I mean, who wouldn’t want to ditch passwords forever? I think that web developers that implement Passkeys into their services are about to boom.
Passkeys are a joint initiative from Apple, Google and Microsoft and I presume that soon we will be using Passkeys in all our devices, independently of the vendor and start thinking that passwords are just a thing from the past.
Lockdown mode
Creating secure devices is a tough task. Apple has learnt that the hard way. Recent scandals such as the Pegasus infections have put Apple’s actual security of its devices and Operating Systems on doubt.
Lockdown mode is Apple’s response to the latest attacks with highly sophisticated malware to their iOS based devices, which by the way, is not the ideal solution, because it means that Apple is actually recognizing that its product are not safe enough for highly targeted individuals and they only way to protect them a bit more is just to disable certain features.
Lockdown mode is a new configuration of iOS in which certain features are restricted or even disabled. These restrictions are activated after the user selects to run in this mode after a restart of the device.
Using Lockdown mode reduces the attack surface of iOS by:
Disabling Facetime incoming calls from unknown users.
Disabling most of the files that can be shared through Messages app and disabling link previews.
Features in the browser are disabled: Web fonts won’t load and the Javascript engine will not use JIT (just in time) compilation. So, web rendering will be affected and also loading times will increase.
Configuration profiles cannot be installed while the device is under the lockdown mode. To install new ones, the user should disable it, install the profile and re-enable it.
To use USB accessories or to connect your iPhone to a computer the device must be unlocked.
A couple of notes regarding the measures taken in the browser:
Apple forces every web browser (not only Safari) to use its WebKit based rendering engine. There is no way to work around that. Therefore, every web browser will be applying the same security measures as Safari.
I have personally tried Lockdown mode in the iPhone and the web browsing gets a little bit impacted. Specially on those sites who rely heavily on icon rendering through web fonts (which are most of the pages I visited). Other than that, I haven’t seen any other downsides to my normal activity on the phone.
This week’s highlights in tech & cybersecurity
Tesla’s model Y can be unlocked and started by performing an NFC relay attack: The attack requires 2 attackers working in conjunction. Researchers say that the attack takes 2 seconds and lowering the timeout for the NFC authentication to about 0.5 seconds would increase the difficulty to perform this attack. The authors of the attack comment that this attack could be performed on other manufacturer’s vehicles that do not have mitigations like the use of a PIN to start the engine, like Tesla does.
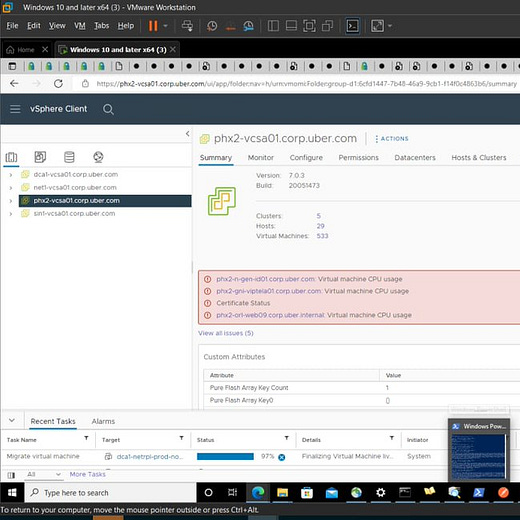
Uber fail - “Security Response Break the glass account”: Uber has been hacked allegedly by an 18 year attacker, who social engineered some workers. Leaked screenshots show how bad the breach is: the attacker accessed to the administrator dashboard of Uber’s infrastructure. The attack is still under investigation.
Bonus: Check the redacted screenshot for the account names…
Ethereum has finally merged: Ethereum, from September 15th, is finally based on proof-of-stake instead of proof-of-work. The most evident benefit is that Ethereum reduced its global energy footprint by ~99.95%.
Have i been trained ?: A website to find images that have been used to train AI models capable of generating images.
EU Cyber Resilience Act: New law project to enforce cyber security measures to the digital markets throughout the life-cycle of the products.
❤️ My favorite things
Michale Driscoll illustrated network protocol and cryptography collection: The animated Elliptic Curve, the illustrated TLS 1.3 connection and QUIC connection are perfect learning materials for those of you who want to know more about them. These resources are visually appealing and make easier to understand what’s beneath the protocols, and the math behind Elliptic Curve.